Believe it or not, utilizing Server-Side Encryption on Amazon S3 is simpler than you might imagine!
Securing your data is essential to maintaining compliance regulations, protecting confidential information, and preventing malicious actors from accessing sensitive information. With server-side encryption on Amazon S3, you can store your data securely and protect against unauthorized access. This guide provides an overview of server-side encryption on Amazon S3, how to enable and configure it in your account, and tips for managing your encryption keys. Read on to learn more about server-side encryption and how it can help keep your data safe.
What server-side encryption is
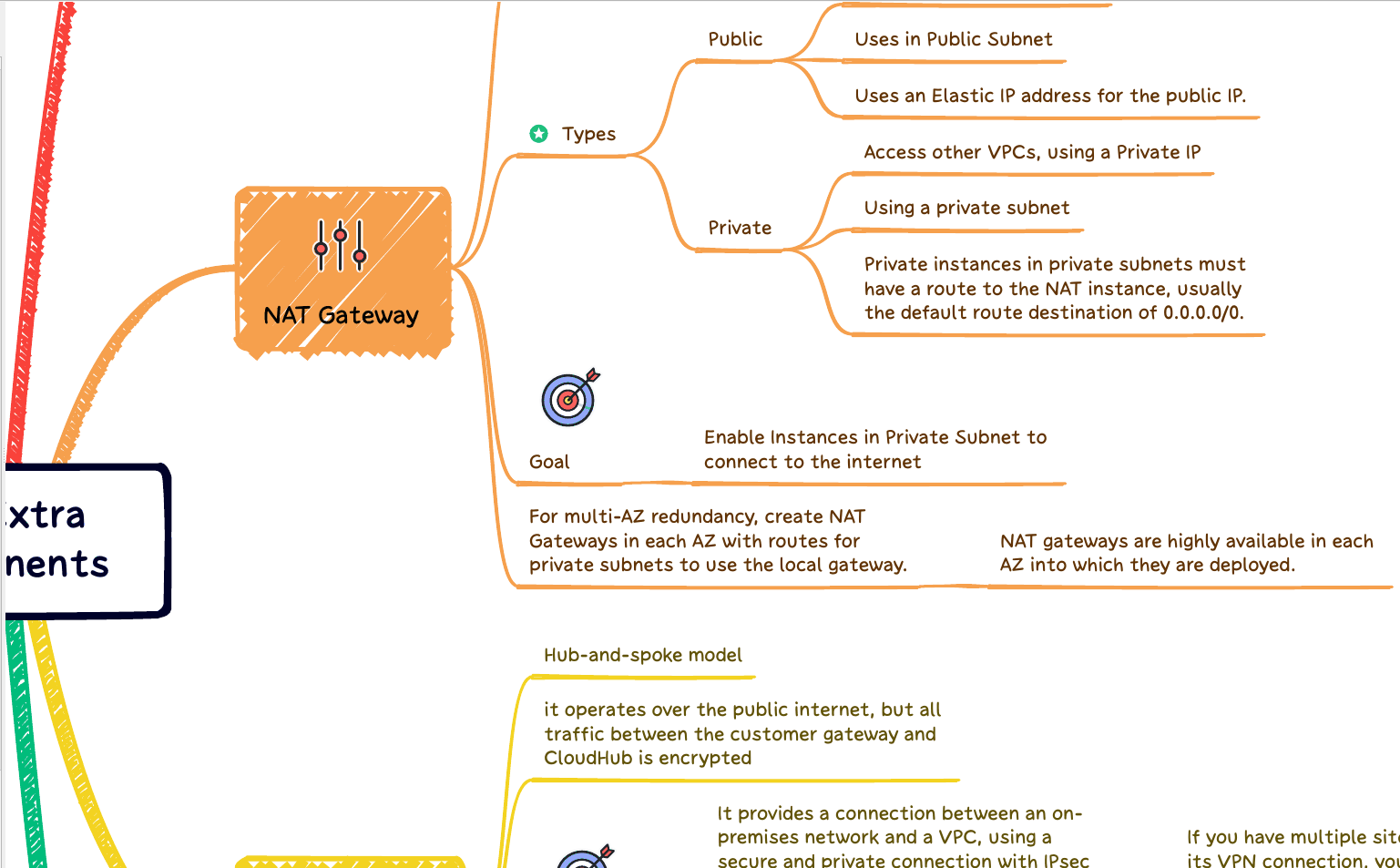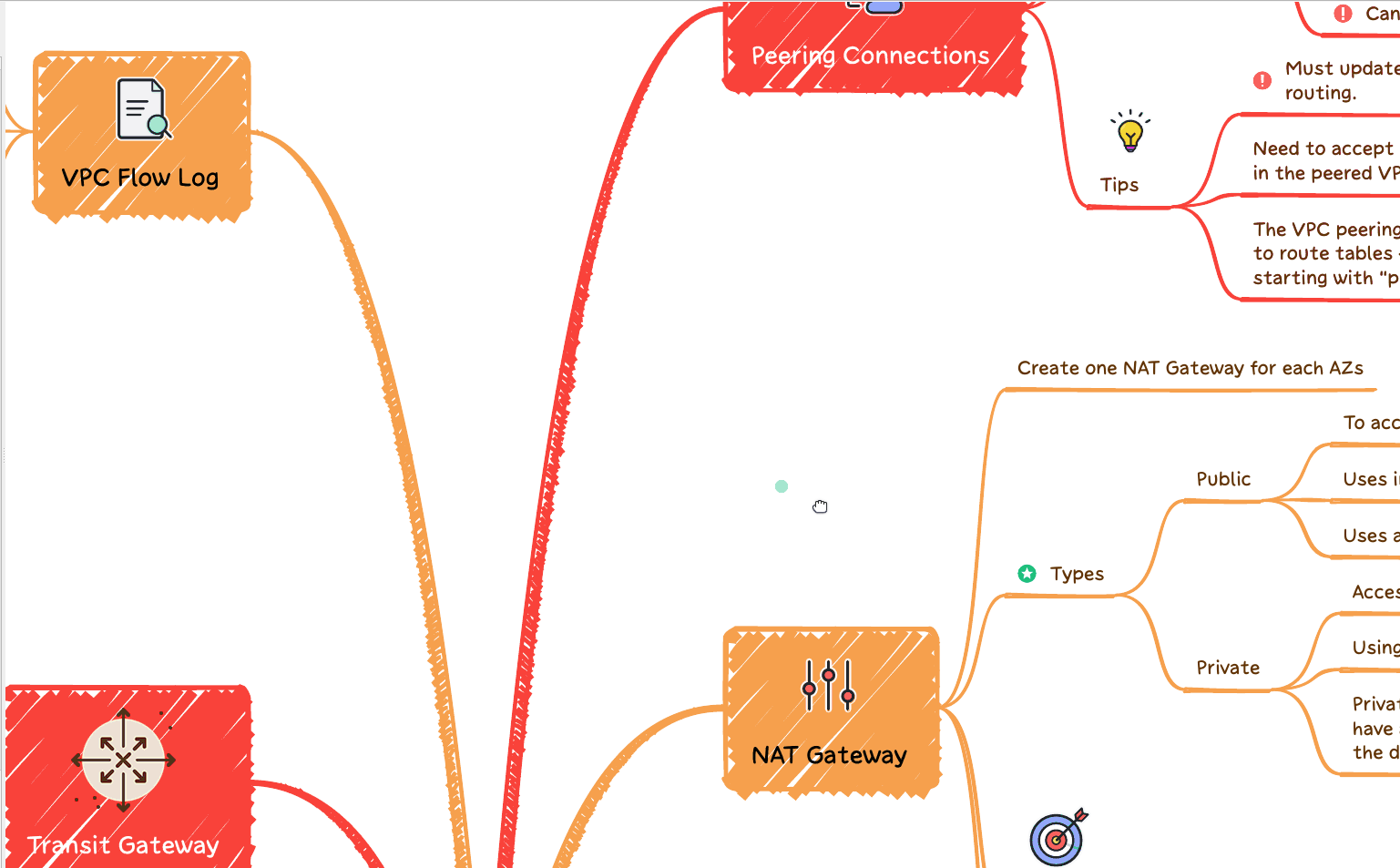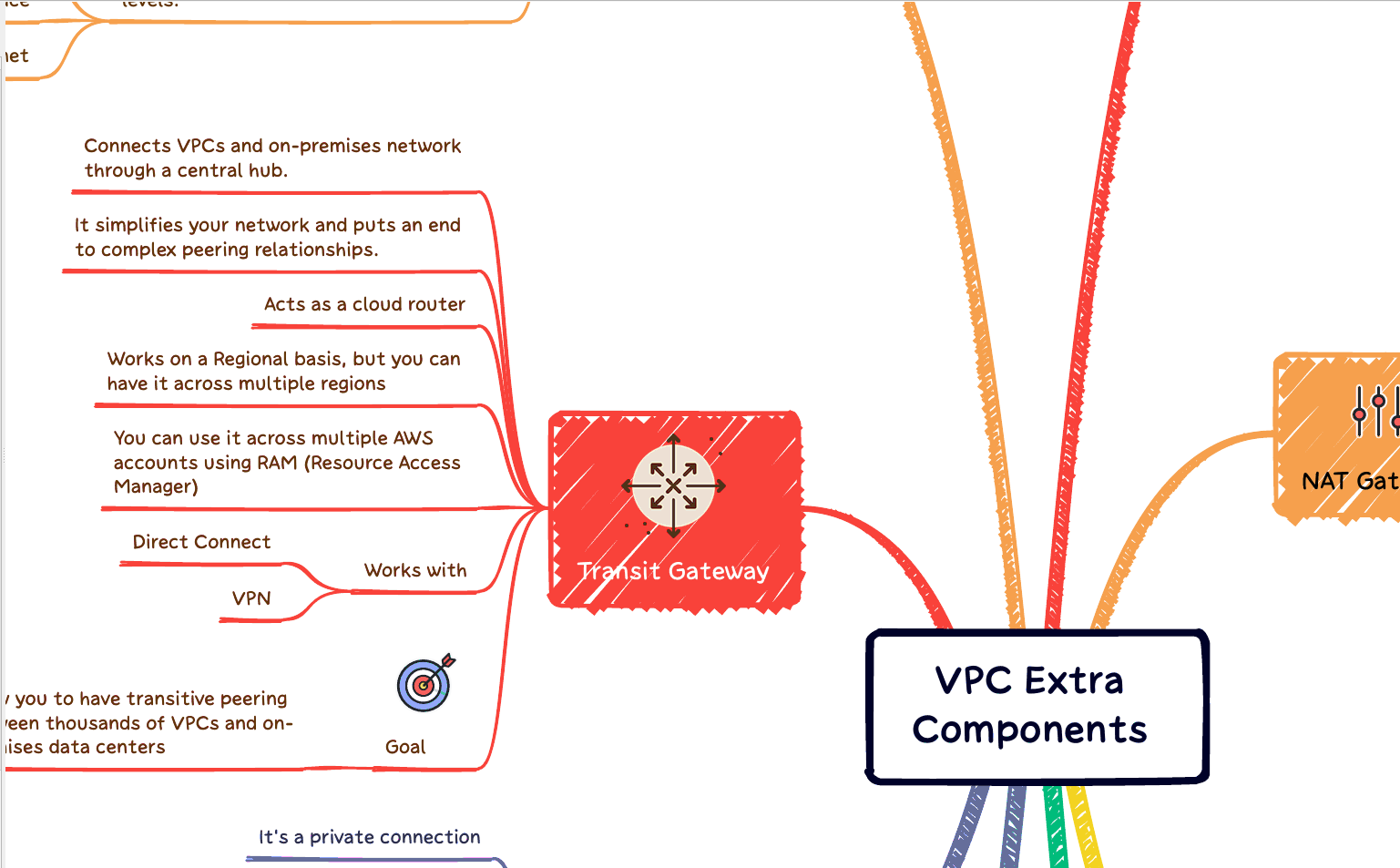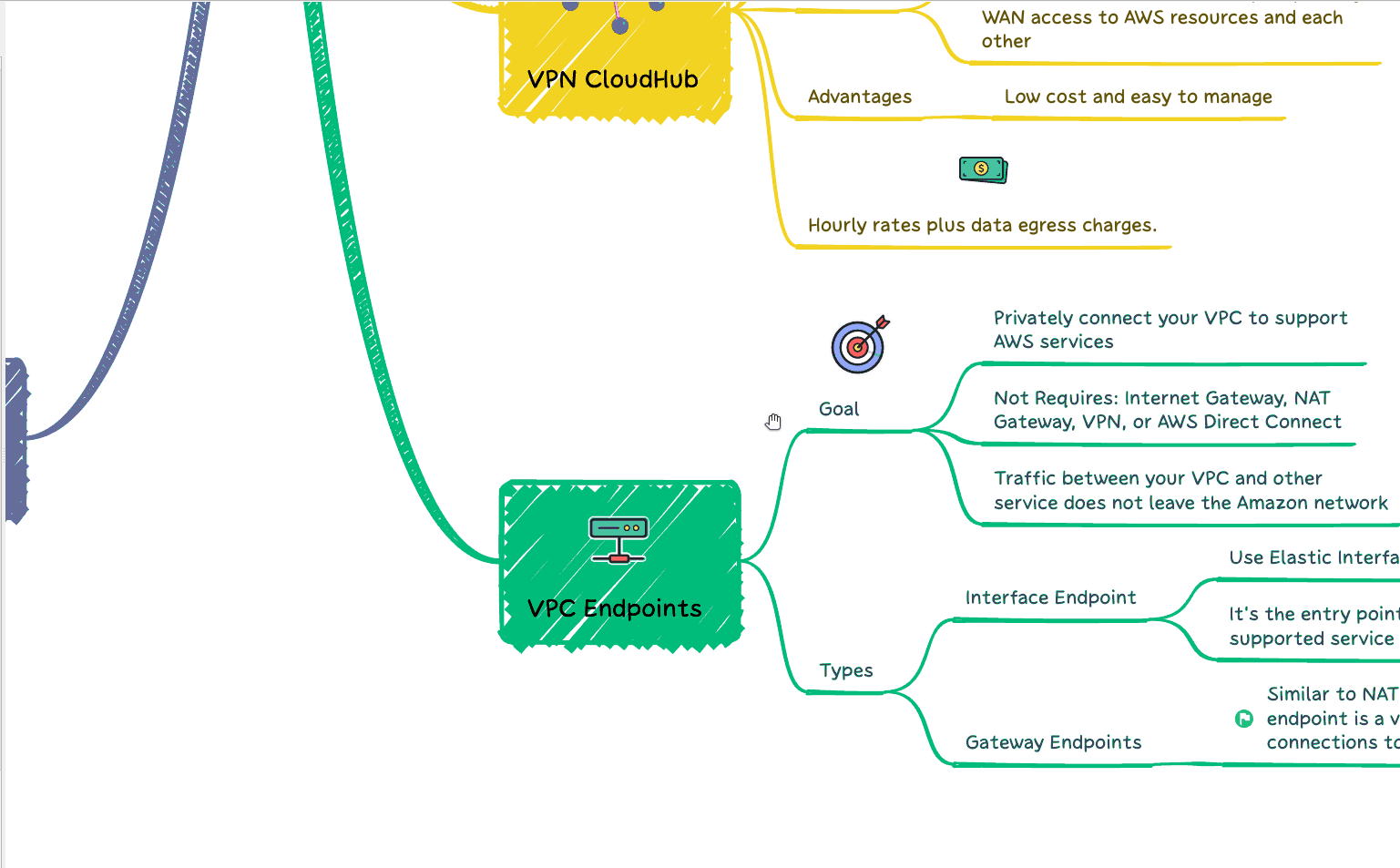
Server-side encryption is an additional layer of security for data stored in Amazon S3 buckets. It uses server-managed keys (SSE-S3) or customer-managed keys (SSE-KMS) to encrypt the objects stored in your buckets. With SSE-S3, Amazon S3 manages the encryption keys, while with SSE-KMS, you maintain complete control over them. Both methods ensure that data is protected if it is intercepted or accessed without authorization.
Server-Side Encryption on Amazon S3: Types of Server-Side Encryption
The two types of server-side encryption on Amazon S3 are SSE-S3 and SSE-KMS. With SSE-S3, Amazon S3 manages the encryption keys and encrypts all data stored in your bucket with a unique key. With SSE-KMS, you maintain control over the encryption keys and can rotate them periodically for enhanced security. In either case, all objects stored in your buckets are encrypted and protected from unauthorized access.
Customer-provided keys (SSE-C) are an additional type of server-side encryption on Amazon S3. With SSE-C, you provide a unique encryption key for each object stored in your bucket. This ensures that the data is encrypted using customer-provided keys and can only be decrypted with the same key.
SSE-C is an excellent option for organizations that require strict control over their encryption keys and need to rotate them periodically for enhanced security. It is also helpful for storing sensitive data, such as healthcare or financial records, that require additional encryption and protection.
AWS-managed KMS key with S3
You need to be aware of a limitation when you use the AWS-managed KMS key with your S3 Bucket.
Sometimes, you can see this question: Why are users with cross-account privileges denied access when attempting to retrieve objects encrypted using a custom AWS KMS key from Amazon S3?
Though AWS-managed KMS key policies are unchangeable due to their read-only status, you can view them alongside customer-managed key policies at any time.
AWS-managed KMS key policies are immutable, meaning that cross-account permissions for these policies cannot be granted. Additionally, encrypted objects from an outside account cannot access the customer’s respective KMS keys. On the other hand, if your organization utilizes a Customer-Managed Key Policy, you can adjust it only through its
How to resolve this issue?
You need to use Customer-Managed Key, and then:
To enable a user in Account Z to access an AWS KMS-encrypted bucket situated in Account X, the necessary permissions must be configured appropriately. Specifically, the bucket policy must allow explicit access from Account Z, while the accompanying AWS KMS policy must grant users located within this account authorization for optimal security.
Additionally, The IAM policy of Account Z needs to be given privileges over the protected storage and its corresponding encryption key stored in Account X to give the full user access.
New changes for 2023
On January 5, 2023, AWS revolutionized data security with a fantastic announcement – server-side encryption with Amazon S3 managed keys (SSE-S3) is now the default! The best part? Amazon S3 has revolutionized how we protect our data by automatically encrypting all new uploads without any costs or negative impacts on performance. This momentous development sets a gold standard for information safety and security, ensuring that everyone can stay secure in an ever-changing digital world.
Server-Side Encryption on Amazon S3: How to enable
Enabling server-side encryption on Amazon S3 is a simple process. To use SSE-S3, you can set the server-side encryption configuration in your bucket policy. To use SSE-KMS, you must create and manage your encryption keys in the AWS Key Management Service (KMS) console. Once you’ve set up your keys, you can easily enable SSE-KMS encryption in your Amazon S3 bucket.
Best practices and Tips for Managing Encryption Keys
Encryption keys are a critical component of server-side encryption, so it’s essential to maintain control over them. Here are some best practices for managing your encryption keys:
– Rotate your keys regularly, including when they are used to encrypt new data or when a key is compromised.
– Store your keys in a secure environment, such as an AWS Key Management Service (KMS) or an AWS Identity and Access Management (IAM) policy.
– Monitor your encryption keys for changes to ensure they remain secure and up to date.
– Implement a backup plan in case your keys are lost or compromised.
By following these best practices, you can ensure that your encryption keys remain secure and up to date.
The Need for Rotating Encryption Keys. Do we need to worry about it?
Yes, it is crucial to rotate encryption keys regularly in order to maintain a secure environment. The process of rotating keys involves replacing an existing key with a new one, which helps prevent attackers from gaining access to your data. This also ensures that new data remains encrypted with the most up-to-date key and is not vulnerable to attack.
Rotating encryption keys is a simple process that can be done manually or with automation tools. Most vendors offer automated key rotation solutions, which automate generating and replacing new encryption keys. These solutions allow organizations to keep their data protected without manually updating their encryption keys every time new data is added.
Additionally, these solutions are often integrated with existing data management systems and can be used to update encryption keys across multiple platforms quickly.
As encryption keys play a critical role in protecting data, it is essential for organizations to ensure that they are securely managed and updated. Regularly rotating encryption keys help protect organizations’ sensitive data from attackers and ensure that their data remains secure. Therefore, it is essential for organizations to have a comprehensive key-rotation strategy to ensure their data’s security.
What are the benefits of using server-side encryption on Amazon S3?
Using server-side encryption on Amazon S3 offers numerous benefits, including enhanced security and improved performance.
Security: Server-side encryption provides an extra layer of security to all objects stored in your Amazon S3 buckets. This helps protect against unauthorized access and ensures that only authorized users can access the data, even if they are able to gain access to the server. Additionally, server-side encryption helps protect sensitive data from malicious actors and can be used to comply with data privacy regulations.
Performance: By using server-side encryption, organizations can improve the performance of their applications. Server-side encryption takes away some of the processing power required for data decryption, allowing applications to run faster and more efficiently. Additionally, this reduces infrastructure costs associated with managing encryption keys.
How to Monitor and Auditing Encryption Keys
When you enable encryption on Amazon S3, with SSE-KMS encryption, you must ensure that your encryption keys are monitored and audited regularly. Monitoring and auditing help organizations detect any changes or irregularities in their encryption keys, which can alert them to potential attacks or malicious activities.
Using SSE-KMS encryption for Amazon S3 adds an extra layer of security to help protect against unauthorized access. Through this encryption, the objects stored in your Amazon S3 buckets are encrypted, and only those with permission can decrypt them.
Additionally, by using Key Management Service (KMS), you can monitor who has access to the encryption keys and track every person accessing the S3 objects. This allows you to control who gets access to your data, providing an audit trail that can be used for compliance and governance.
Important Considerations
Furthermore, using KMS provides centralized control over encryption keys, allowing you to manage security policies better and easily change key permissions. With data encryption, SSE-KMS allows you to ensure your data is secure and protected at all times.
Overall, using SSE-KMS encryption for Amazon S3 provides an extra layer of security that can help protect against unauthorized access. It also offers centralized control over the use of encryption keys. It helps track every person accessing the S3 objects, allowing you to control who gets access to your data and provide an audit trail for compliance and governance purposes. Using this encryption, you can rest assured that your data is always secure and protected.
Example
In order to monitor and audit encryption keys effectively, organizations should have a comprehensive strategy that includes the following best practices:
– Regularly monitor your encryption keys for any changes. This can be done using automated systems or manually by reviewing logs and audit trails.
– Audit access to encryption keys and ensure only authorized users have access.
To effectively monitor and audit encryption keys, organizations should use a combination. Of automated solutions and manual review. This ensures that encryption keys are kept up to date, and any suspicious activity is detected quickly and addressed.
How to learn more about
Learning more about cloud computing security is essential for organizations looking to make the most of their cloud infrastructure. Organizations can gain access to various resources, including webinars, articles, and even certifications, to help them understand best practices for securing data in the cloud.
Additionally, they can turn to industry experts and think tank reports to gain insights on protecting their data in the cloud. Also, you can download our AWS Learning Kit to understand AWS better.
Also, you can read our post about AWS Secret Manager and Protect Passwords in Cloud [Full Project Review]
By leveraging the right resources, organizations can take advantage of the benefits provided by cloud computing while also keeping their data secure and protected. With server-side encryption on Amazon S3, they can add an extra layer of security to help protect against unauthorized access and ensure that their data is always secured.
Additionally, they can monitor and audit encryption keys effectively to ensure that any changes or irregularities are detected quickly. With the right cloud security strategy in place, organizations can take advantage of the power of cloud computing while ensuring the security of their data.
Organizations that want to ensure their data is secure should stay up-to-date with the latest security trends and developments, and best practices for cloud computing. This can help them make informed decisions about securing their data in the cloud.
Conclusion
Server-side encryption on Amazon S3 offers an additional layer of security for data stored in your Amazon S3 buckets, helping to protect against unauthorized access. By using Key Management Service (KMS), you can monitor and audit who has access to the encryption keys, allowing you to control who gets access to your data and provide an audit trail that can be used for compliance and governance.
Organizations should also have a comprehensive strategy to monitor and audit their encryption keys regularly. This includes using both automated solutions and manual review to ensure that encryption keys are kept up to date and any suspicious activity is detected quickly. Organizations should stay up-to-date with the latest security trends, developments, and best practices for cloud computing to ensure their data is secure.
Overall, SSE-KMS encryption effectively protects your data stored in Amazon S3 buckets from unauthorized access. You can ensure your data is secure and protected by monitoring and auditing who has access to the encryption keys.